 Telecommunication vendors are in the middle of two technological revolutions that are driving the industry forward – the evolution of 5G networks and the transition to open radio access network (oran) architectures. Network architects are no longer bound to proprietary hardware and software, so they can mix and match network components that best fit the needs of their designs. The disaggregation is a direct complement to 5G use cases such as edge computing that demand networks be more flexible and handle increasing amounts of data processing power.
Telecommunication vendors are in the middle of two technological revolutions that are driving the industry forward – the evolution of 5G networks and the transition to open radio access network (oran) architectures. Network architects are no longer bound to proprietary hardware and software, so they can mix and match network components that best fit the needs of their designs. The disaggregation is a direct complement to 5G use cases such as edge computing that demand networks be more flexible and handle increasing amounts of data processing power.
With 5G connections expected to surpass 1 billion by the end of 2022, and 4.4 billion by 2027, the telecom industry is accelerating towards a need for networks to be as flexible, secure, and efficient as possible. Low power FPGAs [field programmable gate arrays] offer network architects and hardware designers a chance to deliver all three, with an emphasis on end-to-end security.
FPGAs as hardware roots of trust
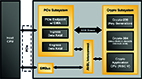
As the radio access network becomes more open, so does the network’s attack surface. Bad actors are constantly seeking out ways to exploit nodes across networks, and hardware designers are relying on platform firmware resiliency (PFR) to combat threats. PFR is a cyber resiliency system that networks can use to proactively protect themselves before, during and after an attack while remaining functional. Achieving PFR requires leveraging a device to act as a hardware root of trust (HRoT) to verify whether a device’s firmware has been compromised at any point in its lifetime.
FPGAs can serve as HRoT and have been used by hardware designers to achieve PFR due to their flexibility and small size, but they are becoming more common in network designs because of the security demands of oran. As long as they have built-in cryptographic capabilities, FPGAs can ensure all incoming and outgoing firmware data is encrypted and decrypted so firmware updates can be performed as securely as possible.
By leveraging FPGAs as a HRoT, a foundational layer of protection can be created for networks to operate securely without hardware designers having to sacrifice flexibility in their designs.
Protecting data
While hardware designers can rely on FPGAs as a HRoT to protect the integrity of firmware anywhere in the supply chain, they must also ensure any network function or user data communicated between any two endpoints across a network remains secure. This process requires following a zero-trust security model and is increasingly critical to the security of networks as oran systems become full of different hardware and software from various vendors.
All components within a system must use encrypted messages to confirm their authenticity to the host system. This zero-trust security model, known as securing the wire, can be achieved with FPGAs that have built in risc-powered CPU cores. The cores can be programmed to create cryptographic and secure messaging protocols, and since FPGAs are reprogrammable, they can keep up with the pace of 5G innovation much faster than with an application specific integrated circuit (asic).
The reprogrammability of FPGAs makes them particularly well suited for accelerated scalability without sacrificing security and enabling hardware design to keep up with 5G and oran innovation.
Data synchronisation
Securing hardware elements and data communicated across components are not the only security challenges FPGAs can help to address. They can also be used as a timing resource to secure data synchronisation connections. As more 5G connections communicate data across a network, the bigger the risk for high latency – especially at the edge – minimising the lag required to achieve end-to-end security.
In oran systems, data packets must be time stamped under the IEE1588 standard so they can synchronise across all network components.
FPGAs are often leveraged as a timing resource in other applications and are therefore also suitable for oran architectures, given the concurrent and consistent manner in which they operate. FPGAs can be used as a bridge to meet synchronisation demands of functional-split options where radio units and distributed units are disaggregated; this is a commonality in oran system designs.
Just as new network capabilities are being unlocked through 5G and oran, so are security challenges that network architects and hardware designers cannot ignore.
 Electronics Weekly Electronics Design & Components Tech News
Electronics Weekly Electronics Design & Components Tech News
