CMOS microcontrollers and processors suffer from imperfections during the manufacturing process due to the variability in the CMOS processes used. This can lead to atomic-level, random variations in the thickness of the oxide layer on silicon wafers.
 There are several ways to exploit the physical phenomena that result from these imperfections to produce random numbers, or seeds. These seeds can be used to create a unique identity for each chip, rather like a fingerprint. This exploitation results in the removal of a major headache and cost when it comes to securing the device. That headache is the need to inject and protect, often termed “provision”, cryptographic keys into the device.
There are several ways to exploit the physical phenomena that result from these imperfections to produce random numbers, or seeds. These seeds can be used to create a unique identity for each chip, rather like a fingerprint. This exploitation results in the removal of a major headache and cost when it comes to securing the device. That headache is the need to inject and protect, often termed “provision”, cryptographic keys into the device.
The generation of a truly random seed, based on the silicon structure of an individual chip, is known as a physical unclonable function or PUF. It can be useful in embedded system devices such as the sensors and actuators deployed in IoT applications.
IoT devices, most of which contain microcontrollers or other CMOS processors, connect over the internet to cloud platforms such as Amazon AWS or Microsoft Azure, or to on-premises servers that host applications and services. There are billions of IoT devices around the world and often thousands within a large industrial installation, providing a large and tempting attack surface for hackers.
To minimise risks to the network, the host platforms must be able to authenticate the unique identity of each IoT device and there must be a way for each device to prove its identity; this process is called attestation. All communications between IoT devices and application platforms must be secure, hence the need for cryptographic keys.
The risks of key injection
Device identities and cryptographic keys are random numbers and the traditional approach is to inject these numbers into the memories of MCUs or into the memories that they access. This is done, often by a third party, using a hardware security module (HSM), which is a computer designed specifically for the task.
The identities of IoT devices and their cryptographic keys are usually injected and stored in MCUs or their associated memory chips (Figure 1), but this is a risky technique.
The main downsides to this approach are entrusting security to a third party, the randomness (sometimes called the ‘entropy’) of the numbers generated by an HSM, which may not be that good, and the fact that identities and keys need to be stored in the devices’ memories. Criminals have established techniques for hacking memories to extract the numbers stored in them, principally through so-called side-channel attacks, where various physical parameters of the memories are measured to extract the information.
The popularity of PUFs
The weaknesses of the key injection process have made chips with integral PUFs more attractive to semiconductor companies and their customers.
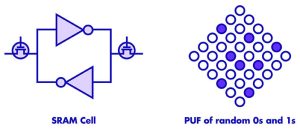 First-generation PUFs are often based on SRAM. When SRAM cells, each comprising four transistors, are powered up, they do so in a preferred state, either a 0 or 1 (Figure 2). The random variations in the thickness of the oxide layer at a particular location determine the outcome. The patterns of 0s and 1s function as a source of random numbers. No key injection is needed, saving costs and supply chain complexity, and device identities are not stored, making them harder to hack.
First-generation PUFs are often based on SRAM. When SRAM cells, each comprising four transistors, are powered up, they do so in a preferred state, either a 0 or 1 (Figure 2). The random variations in the thickness of the oxide layer at a particular location determine the outcome. The patterns of 0s and 1s function as a source of random numbers. No key injection is needed, saving costs and supply chain complexity, and device identities are not stored, making them harder to hack.
Both Microsemi and Xilinx [now AMD] have adopted SRAM PUF technology in FPGAs. NXP uses it in MCUs for IoT applications. The PUF generates a single, unclonable 256-bit number, a seed, from which unique identities and cryptographic key pairs are generated.
SRAM PUFs do have limitations, however. Multiple cryptographic keys are often derived from the same original seed, which means they are mathematically correlated and, potentially, easier for hackers to discover.
Another limitation is that start-up states may be inconsistent – perhaps with error rates of up to 30%. Algorithms can be used for error correction, but in MCUs with limited resources, as is often the case in IoT devices, the additional processing overhead is undesirable.
A second-generation PUF
Second-generation PUFs look set to eliminate the constraints of SRAM PUFs and are being evaluated for new MCU designs by some of the world’s leading semiconductor manufacturers.
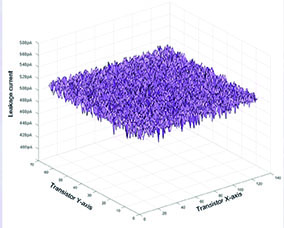
For example, Crypto Quantique’s QDID technology is a dedicated IP block comprising arrays of transistor pairs. The differences in leakage current between the individual transistors in each pair are measured and compared. The levels involved are in the picoA region. These differences are caused by the variations in thickness of the CMOS wafer oxide layer and the resulting quantum tunnelling of electrons across this layer.
Quantum tunnelling is a probabilistic phenomenon by which a tiny particle can pass through a solid barrier, given certain conditions (Figure 3). It is inherently random, so produces random numbers with exceptionally high entropy (randomness), such that it would take vast computing power to predict these numbers.
 QDID technology has been implemented and demonstrated in 55nm and 22nm process nodes. Using this technology, multiple, uncorrelated chip (and hence device) identities and cryptographic keys can be generated on demand – eliminating the need to store any of these in the device memory.
QDID technology has been implemented and demonstrated in 55nm and 22nm process nodes. Using this technology, multiple, uncorrelated chip (and hence device) identities and cryptographic keys can be generated on demand – eliminating the need to store any of these in the device memory.
The technology is ready for devices needing EAL4+ certification, is PSA Certified Level 2 Ready, and has been independently verified as “secure against all known attack mechanisms”.
Without the imperfections inherent in CMOS MCUs and processors, PUFs would not be feasible. Now they are becoming the foundations of IoT device security, and improving in leaps and bounds with each new generation of the technology.
 Electronics Weekly Electronics Design & Components Tech News
Electronics Weekly Electronics Design & Components Tech News



