Called PDID (programming and debugging interface disable), “when enabled, this enhanced code protection feature is designed to lock out access to the programming-debugging interface and block unauthorised attempts to read, modify or erase firmware”, according to Microchip.
The company pointed out that hacking via a programming or debug interface is often possible over a web connection.
“The programming and debug pins on any MCU are also shared with other functions of the chip,” Microchip told Electronics Weekly. “This means that whatever’s connected to those pins ostensibly have access to the port. A hacker who has managed to corrupt other parts of the system in a cloud-based attack can figure out how to reprogram the contents of an MCU, given that the program-debug port is still active. In fact, plenty of existing cloud-connected embedded systems are designed to have their devices re-programmed via the cloud, so the facility is there for hackers who don’t have physical access to the system as part of its design.”
The new one-time disable is implemented on the PIC18-Q24 family of MCUs, and works with the ICSP (in-circuit serial programming) interface.
Once the PDID configuration bit is turned on “the device is permanently locked down from ICSP access and no further bulk-erase operations are possible”, explained the company. “However, the memory regions can still be accessed using the internal NVM [non-volatile memory] interface. This feature is intended to make the device one-time programmable through the ICSP interface for security applications.”
The PDID bit can be programmed either through ICSP or a self-write, and after this it is not possible for a device executing in ‘debug mode’ to erase or write flash memory, nor can a debug tool switch the device to ‘production mode’.
To allow failure analysis in devices with PDID in operation, limited ICSP function can be restored, but only by boot-loader code stored in the device that programs a specific unlock sequence. This will allow ICSP read commands to be performed, while writing to program flash, performing bulk erase, performing page erase, and reprogramming the device via ICSP, will remain blocked.
“The user must program the bootloader code into the MCU before they lock the device,” the company emphasised to Electronics Weekly.
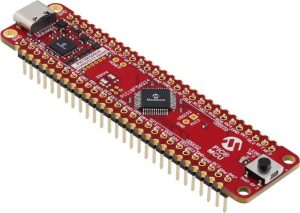
Development tools include the Microchip PIC18F56Q24 curiosity nano eval kit (pictured).
For more PDID information, seek chapter 8.2.5 of the PIC18-Q24 data sheet
 Electronics Weekly Electronics Design & Components Tech News
Electronics Weekly Electronics Design & Components Tech News