Software designed to detect child abuse images on smartphones, which could be mandated by governments in some counties, can be covertly repurposed to intrude on personal privacy, according to research at Imperial college. ‘Client-side scanning’ (CSS) is an image analysis technique based on ‘perceptual hashing’, and is mooted as a way to get around the legitimate problem of criminals hiding ...
Tag Archives: phone
Phone data predicts Covid19 surges
Canadian researchers have used mobile phone data to reveal how much out-of-home travel (dubbed ‘mobility’) is needed to cause a surge in Covid-19 cases. The team uses almost a year’s anonymised phone data (March 2020 to March 2021) to estimate on average how long people were moving outside their homes in Canada, and also noted the week-on-week increase in Covid-19 ...
Do DECT phones have programmed-in obsolescence?
I have been contacted by someone who has had at least two sets of DECT phones – wireless walk-around-the-house phones – and all of them stopped working after five or six years. His suspicion is that they were programmed to self-terminate in a form of built-in obsolescence. And his question is: has anyone else’s DECT phones stopped working without obvious ...
Bosch improves accelerometer-gyro chips for phones
Bosch Sensortec has launched a family of mems inertial measuremnt units (IMUs), aimed at phones, with Android compliance, an I3CSM interface, and support for sensor synchronisation. Called the BMI260 family, the devices combine Bosch Sensortec’s accelerometer with Bosch’s automotive gyroscope, and are claimed to be robust against temperature fluctuations and PCB stress. “Our next-generation IMUs builds upon the BMI160,” said Bosch Sensortec ...
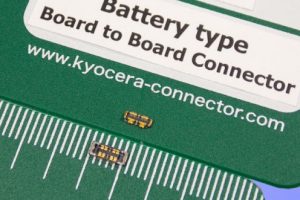
Tiny battery connector handles 10A for faster charging
Kyocera has managed to squeeze 10A capability into a 2.2 x 5.64mm board to board connector with 0.7mm stack height. Part of the 7129 series, it is intended to allow high battery charging currents in portable devices such as smartphones, tablets and wearables. It also includes two signal pins. According to the firm, it has metal guides to prevent mating misalignment damage ...
Geotagged posts on just two phone apps can reveal your identify
Computer scientists at Columbia University and Google have demonstrating that geotagged posts on just two social media apps are enough to link accounts held by the same person – identifying individuals with a high degree of confidence. Location metadata is the key. “If you look unique in how you make phone calls, it is possible to connect that to where ...
A fresh look at bicycle dynamos
As a bicycle dynamo user and interfacer, I am always interested in new dynamo designs. A guy called Nick Zamora, from Florida, has created an open design called CydeKick. By the looks of it, a ring of magnets is mounted on the centre of the wheel and coils are mounted on the frame. An awful lot of power (in bicycle terms, ...
Car hacked through mobile phone connection
US white hat hackers have demonstrated taking control of the engine, and the braking, of a moving car though a mobile phone connection. According to Wired, Charlie Miller and Chris Valase attacked safety critical parts of the car, a Jeep Cherokee, through its ‘Uconnect’ infotainment system. The hackers have been in communication with car maker Chrysler during their attempts, and ...
Tiny thumb trackpad is wireless
For wireless control when hands are full, MIT has invented a thumbnail trackpad called NailO. Stroking it in different directions transmits mouse-like commands to PCs and phones. Even though it sticks on like an artificial nail, packed into the prototype are capacitive sensors, a battery, a microcontroller, and chips for Bluetooth and capacitive-sensing. “The hardest part was probably the antenna ...
Phones vulnerable even when transmitters are off
To make phones and tablets more secure, researchers at the Georgia Institute of Technology are investigating ‘side-channel emission’ – extraneous signals that might assist hackers even though device radios are off. “People are focused on security for the Internet and on the wireless communication side, but we are concerned with what can be learned from your computer without it intentionally ...
 Electronics Weekly Electronics Design & Components Tech News
Electronics Weekly Electronics Design & Components Tech News